10 Easy IT Security Tips for Simple Use in Information Technology

In our technology-driven world, where information flows at lightning speed and digital threats loom large, IT security…

In our technology-driven world, where information flows at lightning speed and digital threats loom large, IT security…

Exploring the Importance of Confidentiality in IT Security: Safeguarding Informational Technology In an age where information reigns…

Understanding the Importance of Documentation in IT Security In the rapidly evolving landscape of informational technology, securing…
In today’s digital age, the convergence of healthcare and technology has transformed the way we manage patient…

In today’s digital landscape, securing your IT systems is paramount. An often-overlooked aspect of this security is…

Analyzing Key IT Cybersecurity Indicators for Information Technology Professionals In the ever-evolving landscape of technology, cybersecurity has…

Understanding the Importance of a Data Protection Incident Report In today’s fast-paced digital world, the integrity of…

Enhancing IT Security: The Importance of Live Fire Drills In today’s digital landscape, where technological advancements are…
The Importance of Data Loss Prevention (DLP) in IT Security In an age where our lives are…
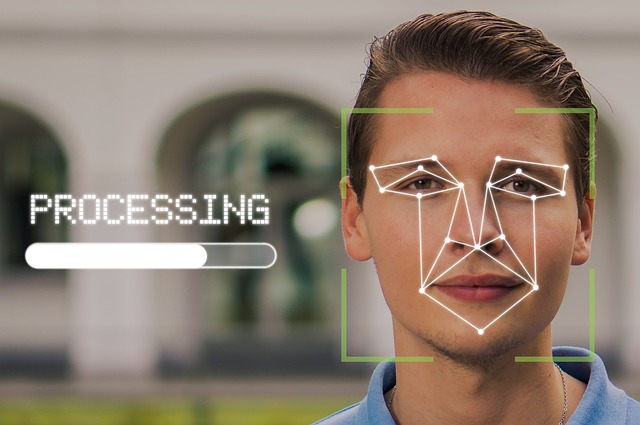
The Future of Biometric Identification in IT Security In a world where technology evolves at breakneck speed,…